Know Your Data
Your data is your greatest asset. Datiphy protects your data in corporate databases, network, servers, and private or public clouds. DatiDNA technology sheds light on your data insight with analysis, compliance, reporting, and intelligence.







Data Intelligence at Your Fingertip
Corporate databases are typically protected by a firewall, behind many layers of business applications – not much thought is given to their potential risk for compromises. These databases contain highly valuable data making them the logical target for malicious attacks. Datiphy’s DatiDNA mapping of all database transactions can help bring these data breach events to light immediately.
What is Database Threat Intelligence?
Simply, it is the information that allows you to “connect the dots” between a user’s behavior and activity, allowing you to detect a potential intrusion or malicious activities.
What are the benefits?
- Gain insight into high-value assets
- Contextualized sensitive data
- Risk analysis of every user, application, and data repository
- Compliance assessment for: GDPR, PCI, HIPAA, SOX, ISO, and SOC
Datiphy Solutions
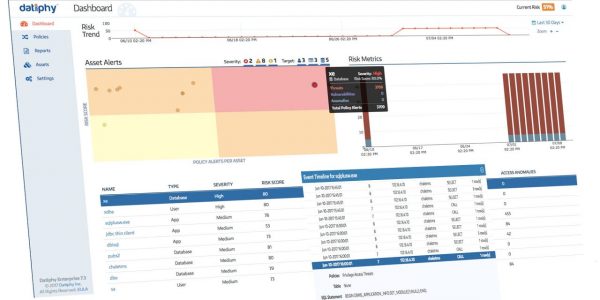
Datiphy Enterprise monitors data on premises and in cloud services using agents on hosts, in the cloud, or on the network. Datiphy Enterprise provides preconfigured threat intelligence rules, as well as risk metrics included out of the box. Pattern matching and machine learning are used to profile users and entities, and detect threats against your database.
RISK ASSESSMENT
THREAT DETECTION

Data-centric Visibility
DatiDNA™
Each data transaction is unique and contains the forensic assets required to build a data-centric view of your business. Every database transaction is processed and all events recorded. By focusing on the complete transaction, data activities and the full context in which they occur are captured.


Data Assets
All assets are extracted in each database transaction, billions of times per day. By analyzing the entire pool, baselines are established and false alarms are eliminated. By automating the harvesting of these key building blocks, the strongest data-centric audit and protection possible is created.

Asset Indexing
Assets are indexed upon extraction and compared to every asset ever witnessed. Changes, including methods and behaviors, are detected immediately and relationships linked. Automated indexing allows users to easily search for any event in plain English and retrieve it instantly.

Data-Centric
Data usage is growing faster than your perimeter and policies can keep up with. Data is also constantly transposed by business processes across multiple silos. Datiphy cross-silo policy management creates visibility to any breaches, regardless of where they take place.

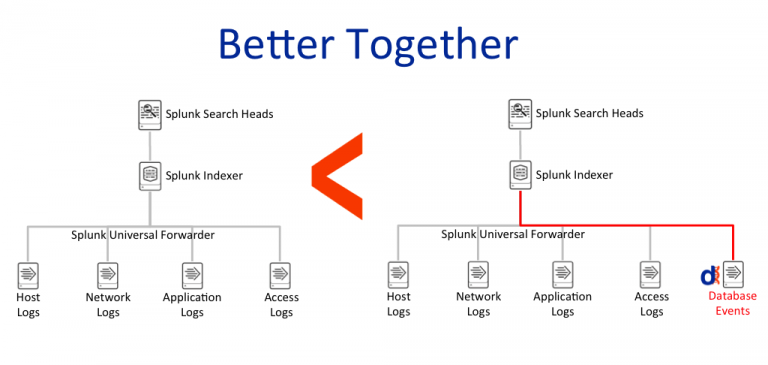
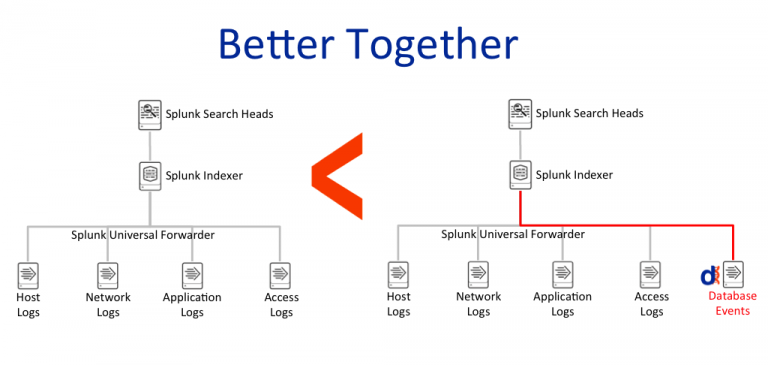
Datiphy Splunk Integration
Datiphy’s agents are pre-packaged with Splunk Universal Forwarder to provide complete data activity monitoring and threat intelligence.
Secure Your Cloud
Datiphy Enterprise Cloud Solution supports many of the existing cloud service providers to ensure that database monitoring is part of your cloud security strategy.

Breach Discovery Gap
Gone
A database breach is inevitable, so knowing exactly when, where and how it is happening is critical. With traditional monitoring methods many silos and gaps exist, allowing breaches to inflict damage for months before being discovered. With Datiphy, customers can for the first time see their entire data life cycle and who is engaging it. Every data asset from billions of transactions each day is sequenced to reveal relationships, behaviors, and methods.
Brand Reputation
Protected
When database breach details are reported in the media, organizations struggle to know exactly what has been taken. Credibility is lost when you can’t provide detailed answers on the scope of the breach. This is the root impact of when your data has been compromised: you’ve lost control. With Datiphy, organizations will know exactly what data has been accessed the moment it occurs and have the framework in place to stop the attack.