Datiphy Executive Overview
Introduction
The Datiphy platform provides industry leading end-to-end data transaction analysis to detect breaches as they unfold. Datiphy automates the extraction and indexing of key data assets from billions of data transactions per day, allowing instant visibility and detailed forensics to the complete data life-cycle. Unlike traditional policy and perimeter based security tools that only provide point protection and lack context, Datiphy provides users with a unique DNA profile of each transaction directly from the data’s point of view. Each asset within the data DNA profile is automatically indexed against all other transactions. The powerful indexing engine identifies relationships that provide the critical context of how sensitive data is living and being accessed within the enterprise. The Datiphy platform is the first true data-centric audit and protection tool.
Data DNA & Scientific Behavior
Every data transaction has a unique series of assets. Datiphy extracts these data assets for every transaction and indexes them in real time. Scientific relationships among the assets are built and their behavior base-lined. Because every transaction is being surveyed vs a sample, any change in behavior is immediately sensed and false alarms are eliminated.
Deep Forensics to Avoid Disaster
Think of Datiphy as the data version of a DVR. Detailed forensics, indexed in real time, allow you to see your sensitive data in action as it flows in and out of the enterprise. Datiphy users can replay events to study the tactics and build policy against similar future attacks or alerts for further discovery.
Cross-Silo Policy Management
Business processes constantly transpose data across multiple silos. This massive data generation and usage is rendering current methods of data security governance obsolete. Datiphy users build and manage data-centric security policies to coordinate controls across these data silos.
Protect Your Brand Reputation
When breach details develop in the media, it is clear organizations struggle with knowing exactly what has been taken. Datiphy detects the breach as it unfolds and teams can react immediately. The damage is limited and executives will know exactly what has been compromised.
Who is Hiding?
Once a user is inside, the User ID disappears and the application server credentials are all that communicate with the database. This is a normal behavior that is often exploited by attackers. Datiphy’s patented user mapping technology will identify these users and map their actions from the initial HTTP request through the back-end database response.
Threat Intelligence & Log Data Merged
The problem with log data is it is overwhelming and lacks relevance. The problem with threat intelligence is most people don’t know what to do with it. Datiphy bridges the gap, giving log data intelligent context and making threat intelligence actionable. Enterprises gain data-driven visibility into the critical information needed to help detect targeted, dynamic, and stealthy attack methods.
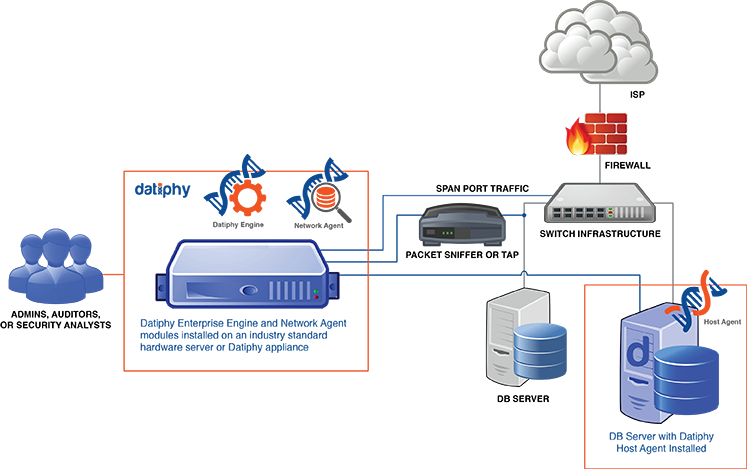
The above diagram represents a typical deployment scenario.
See Relationships with Context
Many tools will provide a glimpse into your data assets, but they lack the complete story. With Datiphy not only will you see the relationships among data assets, but you will also have the complete context in which those assets interact.
See Data Changes
Sometimes accidents happen. Because Datiphy records the details of every data transaction, you can go straight to the event to see what happened and take the appropriate steps for a complete and fast restore.
Search Any Events Instantly
Because Datiphy indexes the elements of every data transaction as it occurs, events are easy to find and the forensics behind them are instantly available. Incident Response teams now have instant root cause forensics at their fingertips. Compliance Team audit tasks become fast and simple. Searching and reporting the who, what, when, where, and how for any event or data asset is a breeze.
See Those Who Observe Data
The pool of read privileges are much larger than the pool of write. Datiphy records the trails of those that take a look at sensitive data, regardless of whether change or take it.
Mean Time to Verification (MTTV)
Too much alert overload and threats go uninvestigated. With Datiphy, responding to alerts with relevant detail in real- time enables teams to validate real threats quickly and conclusively.
Mean Time to Response (MTTR)
Datiphy will eliminate false positives that waste precious time. By focusing on just the facts, teams investigate faster and provide less time for attackers to cover their tracks.
Mean Time to Resolution (MTTR 2)
Discover compromises as they happen and see the relationships among all similar suspicious behavior. Stopping the attack is only part of the job; with Datiphy context, ensuring it cannot happen again finishes the job.
For more information or to request a product demonstration, please visit: www.datiphy.com/schedule-demo/
